Digital payments have become a ubiquitous part of our lives, and with this increased usage comes an ever-growing need for secure and efficient transaction processing. A quick look at the history of card payments tells us that there is a constant focus on innovating and enhancing the security of transactions. Initially we had magnetic stripes on cards, then the industry evolved and moved on to EMV chips for better security and now, we have something called “tokens” which eliminates the need for providing card information altogether.
So what exactly is a token?
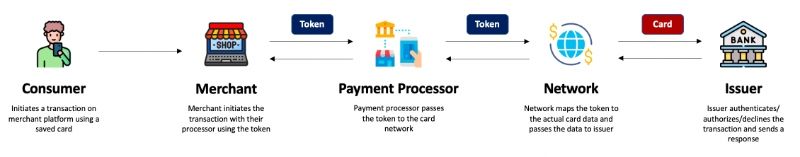
A “token” is a unique digital identifier that is used to replace sensitive card information (PAN and other details). This token is provisioned and managed by the network (e.g. VISA, Mastercard etc.) and can be used for transactions instead of your actual card number. So, instead of using your real card number which can be easily stolen by fraudsters, the token replaces it and becomes the only piece of information needed for transactions.
How does tokenization enhance card security?
Let's first try to understand the scope of a token.
Each token is unique to a specific combination of PAN, device/channel, and merchant. In addition to the token, a cryptogram is generated and sent along with the authorization. This cryptogram is unique to the token and the individual transaction. The token is meaningless to anyone who doesn't have the key to decode it, which makes it useless for hackers who try to steal card numbers. The real card information is only transacted between the network and the issuer and hence potential points of leakage of sensitive card data are considerably reduced, thereby enhancing card security
Types of E-comm Tokenization
Tokenization can be done either at a Device level or at a Server level.
Device Side Tokenization
Through device-side tokenization, tokens are linked to a specific device, making them usable for subsequent transactions only on that same device. For example, if a user were to tokenize their card on Amazon, the token generated will be specific to that device and Amazon.
Device side tokenization is used by payment solutions like Apple Pay and Google Pay, which are primarily app-based payment options. To enable Device Side Tokenization, merchants need a certified SDK offered by payment networks or an approved third-party Token Requestor — TSP.
Server-side or Card on File Tokenization (CoFT)
CoFT generates tokens that are not device-specific, but instead mapped solely to the merchant in question. For example, a card tokenized on Amazon can be used across any of the Amazon (Desktop, Android, Mweb, etc).
Unlike Device side tokenization, CoFT can be implemented by integrating APIs provided by either the Networks or Token requestors
In general, CoFT is the preferable mode of tokenization given it allows interoperability of tokens among different platforms
What’s in it for merchants?
- Up-to-date cardholder information: Since the tokens are provisioned by the networks the mapping of cardholder information to the tokens is also managed by the networks. So even if the underlying card is lost/expired/replaced/reissued, the token can still be used to run transactions on the cardholder’s account and the network will update the card information in the backend. According to Stripe around 40% of cardholders replaced their cards in 2022 and most of them forget to update their new card details with the merchants. Network tokenization can be a boon in such cases
- Improved Authorization rates and Fraud Reduction: Every $1 of fraud now costs U.S. retail and e-commerce merchants $3.75. Network tokenization can be the silver bullet to keep fraud rates at bay. We have already seen how network tokenization eliminates the need for merchants to directly handle any sensitive card information. Even if the tokens were to be stolen, the non-usability of tokens outside of their specific payment context significantly decreases the risk of fraudulent transactions. This instills confidence in issuers and they tend to approve more token based transactions resulting in higher authorization rates. Visa has seen a 2.1% increase in authorization rates and a 26% reduction in fraud as a result of using network tokenization
- Incentives and Liability Shift: For every card transaction merchants pay a transaction fee (interchange fees) to the card-issuing bank to cover handling costs, fraud and the risk involved in approving the payment. To promote the adoption of network tokens, VISA reduced the interchange fees by 10 bps for card-not-present network token transactions from April 2022. Moreover, there might be a liability shift for network tokenization in card-not-present transactions. Typically, any fraud-related charges fall on the merchant; however, with network tokenization, the liability is expected to shift to the issuer, similar to the shift seen with EMV transactions in card-present scenarios
What changes for the customer?
The payments journey largely remains the same for the end customer. The experience would in fact be slightly improved as the customer won’t have to update their card information with the merchant every time it changes.
So is it all win-win? Well, there’s always something!
Sure, network tokenization does enhance card security. But it also implies that all transactions have to flow through VISA and Mastercard. Since these networks provision and maintain the tokens, routing the token based transactions through them becomes essential for decrypting the tokens and passing on the actual card information to issuers.
What’s the disadvantage you ask? Well if you are a large merchant reaping cost savings with the help of least cost debit routing, adopting network tokenization might hamper your plans. For those who are not aware, the 2011 Durbin Amendment mandated debit card issuers to provide at least two unaffiliated card networks capable of processing transactions on their debit card. This allowed merchants to route a debit card transaction to the lowest cost network for that transaction.
Debit card transactions account for ~67.5% of the total card transactions in the US and hence it is important for merchants to understand how they can cut costs using debit routing. Debit card transactions can be processed through signature rails (maintained by VISA, Mastercard, Discover) or through Debit network rails (maintained by regional debit networks like STAR, Accel, NYCE etc.). Regional debit networks process transactions through PIN or PINless technology (for card-not-present scenarios) and avoid the network fees charged by the major networks. Hence routing debit transactions through domestic and regional PINless debit networks helps to bypass the higher interchange fees associated with using signature debit rails
Conclusion
With the the Federal Trade Commission (FTC) stepping in to investigate token restrictions on Card-Not-Present (CNP) debit routing, the existing tokenization barriers might be reduced for regional networks in the future. On the other hand, CNP debit volume is an important part of the puzzle and VISA and Mastercard may not be interested to give up their dominance so easily. When it comes to credit cards, tokenization certainly is a win-win as it enhances security and also ensures a smoother experience for consumers by eliminating the need for updating card information with merchants.
Overall, network tokenization is definitely a powerful step towards more secure card transactions. As the technology continues to evolve, we can expect to see even more innovative use cases emerge in the coming years, and merchants must be ready when the time comes!