Payment frauds are a growing concern with online payments. With the increasing use of online transactions and electronic payments, fraudsters have found new ways to exploit vulnerabilities in the system. In this comprehensive guide, we'll delve into the world of payment frauds, exploring the various categories, types, and the mechanisms through which they occur. Most importantly, we'll provide you with effective solutions to mitigate payment fraud, ensuring a safer and more secure financial environment for both businesses and consumers.
Overview: Categories of Payment Frauds
Before we dive into the specifics, let's take a moment to understand the different categories of payment frauds. Payment frauds can be broadly classified into the following categories:
- Card-Not-Present (CNP) Fraud: Card-not-present fraud occurs when a fraudster makes a transaction without physically presenting the payment card. This type of fraud is prevalent in online and phone transactions, where the fraudster may have obtained the card details through various means.
- Card-Present Fraud: Card-present fraud, on the other hand, involves the physical presence of the payment card during a transaction. Fraudsters typically use techniques like skimming or cloning to obtain card information and then make unauthorized purchases.
- Identity Theft: Identity theft is a broader category of fraud where an individual's personal information is stolen and used to make unauthorized transactions. This can involve opening new accounts, applying for loans, or making purchases in the victim's name.
- Account Takeover: Account takeover occurs when a fraudster gains unauthorized access to someone else's account, typically by obtaining login credentials. Once inside, they can manipulate the account for fraudulent purposes, such as making transfers or withdrawals.
- Payment Processor Fraud: Payment processors are a crucial part of the payment ecosystem. Fraudsters can exploit vulnerabilities in these systems to manipulate transactions or steal funds.
What are the Types of Payment Frauds?
Now that we've covered the categories, let's delve deeper into the specific types of payment frauds that fall under each category.
Card-Not-Present (CNP) Fraud
- Phishing: They involve tricking individuals into revealing their payment card details or personal information through deceptive emails, websites, or messages.
- Carding: It is the process of testing stolen card details by making small purchases to check if the card is active and valid before committing to larger transactions.
Card-Present Fraud
- Skimming: Skimming devices are placed on legitimate card readers, like ATMs or gas station pumps, to capture card information as customers use them.
- Cloning: Fraudsters use a card reader/writer to create a duplicate of a legitimate card, allowing them to make unauthorized transactions.
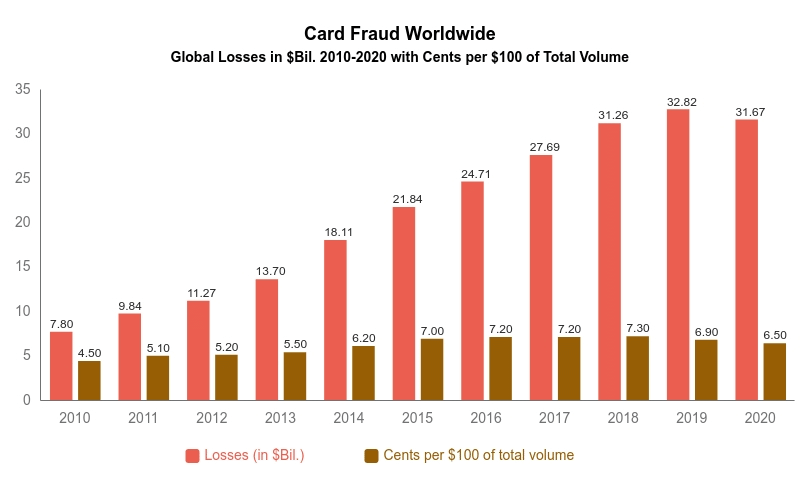
Identity Theft
- Data Breaches: They involve the unauthorized access to and theft of personal data from organizations' databases, which can then be used for identity theft.
- Social Engineering: Fraudsters use social engineering tactics to manipulate individuals or employees of an organization into revealing personal information or granting access to sensitive data.
Account Takeover
- Credential Stuffing: Fraudsters use stolen username and password combinations obtained from previous data breaches to gain access to multiple accounts owned by the same individual.
- Brute Force Attacks: In brute force attacks, fraudsters attempt to guess account credentials by systematically trying every possible combination until they find the correct one.
Payment Processor Fraud
- Unauthorized Transactions: Fraudsters may exploit vulnerabilities in payment processors to initiate unauthorized transactions, siphoning funds from legitimate accounts.
How do Frauds Occur?
Understanding how payment frauds occur is essential for preventing them. Here's an overview of the common methods and vulnerabilities that fraudsters exploit:
- Weak Authentication: Weak or easily guessable passwords and lack of multi-factor authentication make it easier for fraudsters to gain unauthorized access to accounts.
- Phishing and Social Engineering: Fraudsters use cleverly crafted emails, websites, or phone calls to trick individuals into revealing their payment card details, login credentials, or personal information.
- Data Breaches: When organizations fail to secure customer data adequately, cybercriminals can breach their systems and steal valuable information for fraudulent activities.
- Card Skimming and Cloning: Skimming devices placed on card readers or the use of card cloning machines allows fraudsters to capture card data during legitimate transactions.
- Unauthorized Access to Payment Processors: Exploiting vulnerabilities in payment processors can enable fraudsters to manipulate transactions, divert funds, or create fake transactions.
Solutions to Mitigate Fraud
Now that we have a clear understanding of payment frauds and how they occur, let's explore effective solutions to mitigate these risks and ensure a safer financial environment for all:
- Strong Authentication: Implement robust authentication methods such as multi-factor authentication (MFA) to protect user accounts from unauthorized access.
- Education and Training: Educate employees and customers about common fraud tactics like phishing and social engineering to empower them to recognize and report suspicious activities.
- Data Security: Invest in robust data security measures, including encryption, regular security audits, and patching vulnerabilities to prevent data breaches.
- Card Reader Inspections: Regularly inspect card readers, ATMs, and gas station pumps for skimming devices to detect and prevent card-present fraud.
- Monitoring and Analytics: Utilize advanced fraud monitoring and analytics tools that can detect unusual patterns and behaviors in real-time, helping prevent unauthorized transactions.
- Collaboration with Payment Processors: Establish strong partnerships with payment processors and regularly assess their security measures to protect against payment processor fraud.
- Fraud Detection Services: Consider leveraging third-party fraud detection services that specialize in identifying and preventing various types of payment frauds.
FAQs
- What should I do if I suspect fraudulent activity on my account?
If you suspect fraud, immediately contact your financial institution or payment provider to report the issue. They can guide you through the necessary steps to secure your account. - How can businesses balance security with user convenience in online transactions?
Businesses can strike a balance by implementing strong security measures like MFA while providing a user-friendly experience. User education also plays a crucial role in this regard. - Are small businesses as susceptible to payment fraud as larger enterprises?
Yes, small businesses are also vulnerable to payment fraud. In fact, they may be targeted more often due to potentially weaker security measures. It's essential for all businesses to prioritize fraud prevention.
Payment fraud is a persistent threat in today's digital landscape, but with the right knowledge and proactive measures, individuals and organizations can significantly reduce their vulnerability. By understanding the categories, types, and mechanisms behind payment frauds, and by implementing robust security measures and staying vigilant, we can all contribute to a safer and more secure financial environment for everyone. Remember, prevention is key, and together, we can thwart the efforts of fraudsters and protect our financial well-being